Platform Architecture Highlights
KonectIQ provides end-to-end visibility across on-prem, cloud, and remote sites with reduced downtime through predictive alerts and automated remediation.
Shared Control Plane
Unified state store for consistent operations across all modules
Centralized Management
RBAC with tenant isolation for secure multi-tenant operations
Flexible Telemetry
Lightweight agent and agentless collectors for comprehensive monitoring
Edge Intelligence
Optional EdgeBox for local processing and offline resilience
Platform Benefits
End-to-End Visibility
Across on-prem, cloud, and remote sites
Reduced Downtime
Predictive alerts and automated remediation
Improved Security
Zero Trust policies with real-time enforcement
AI-Driven Operations
Optimized via intelligent insights and workflow guidance
Inside KonectIQ: How IT Teams Actually Work
See how African IT professionals are using KonectIQ to manage complex infrastructure with simplicity and precision
Click on image to enlarge
CommandView
Infrastructure Overview
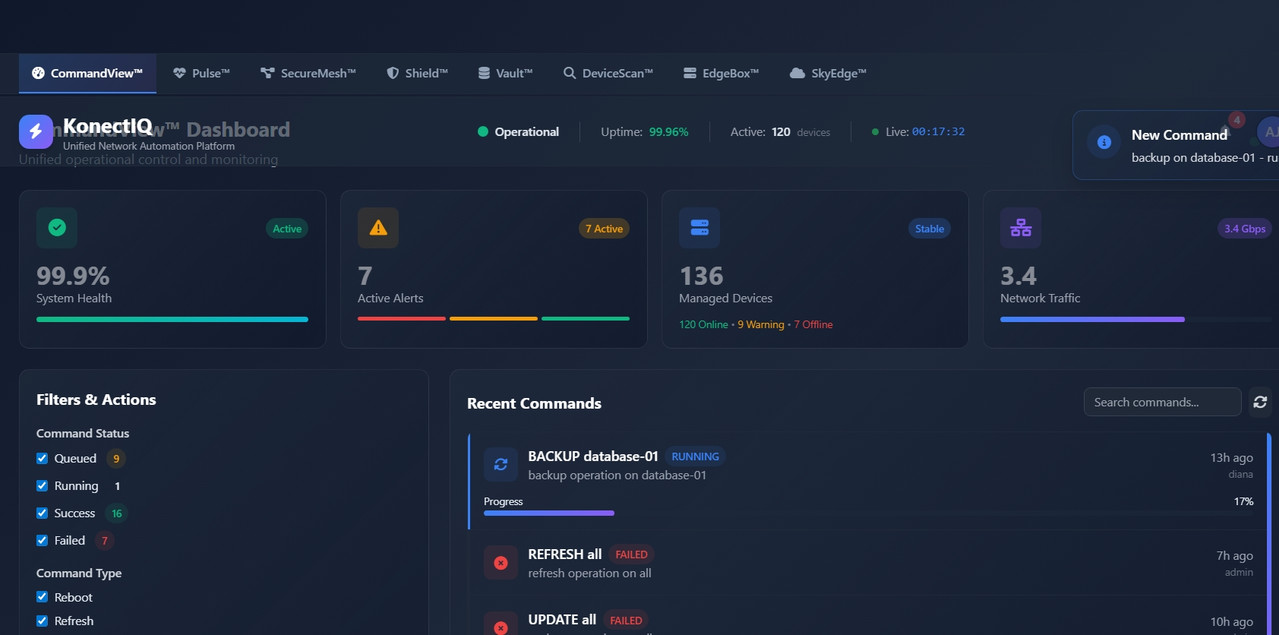
"With CommandView, I can see everything in one place. No more switching between 12 different dashboards."
SkyEdge
Workflow Automation
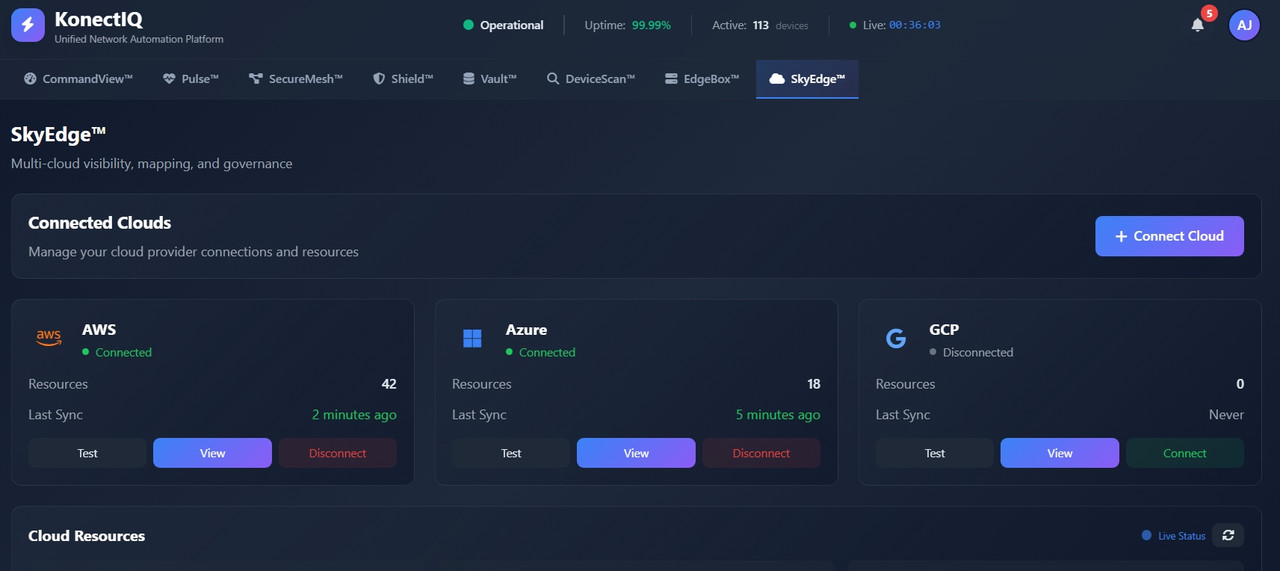
"SkyEdge cut our incident response time by 80%. What used to take hours now happens automatically."
Vault
Backup Monitoring
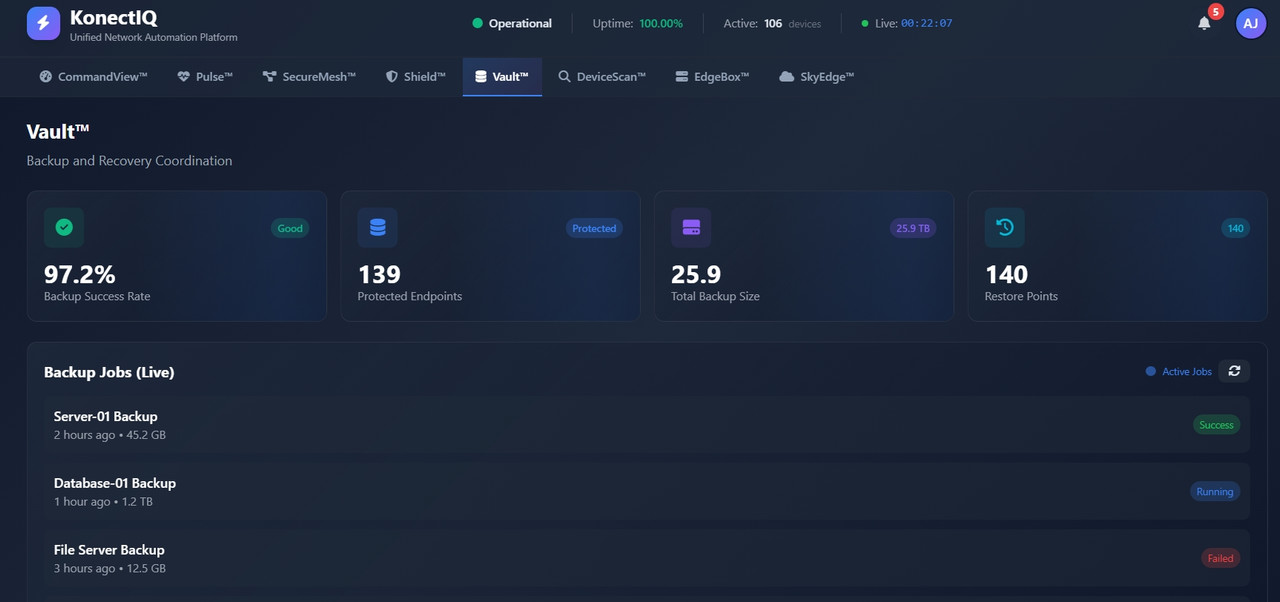
"Vault finally gave us confidence in our backups. We know they\'ll work when we need them most."
Ready to See KonectIQ in Action?
Experience how KonectIQ transforms IT management for African businesses. Schedule a personalized demo to see how our platform can work for your specific needs.
Integrated Platform Modules
Every module, feature, and KAI integration is covered in our unified platform
Unified Operations Dashboard
Your single-pane view of system health across all sites, devices, and cloud environments.
Use Case Example:
Operators view all active tunnels, identify high-risk devices, and immediately see KAI's suggested remediation steps—all from one dashboard.
Telemetry, Metrics & Performance Engine
Collects performance data from all endpoints, devices, and network links, converting it into actionable intelligence.
Use Case Example:
Detect bandwidth saturation before users experience network slowdown and receive KAI-driven recommendations to rebalance loads.
Zero Trust Networking
Provides identity-based connectivity, encrypted tunnels, and policy enforcement across sites and cloud workloads.
Use Case Example:
Branch office experiencing frequent tunnel instability receives automated failover recommendations and routing adjustments.
Security, Detection & Enforcement
Centralizes endpoint security, threat detection, and enforcement across your infrastructure.
Use Case Example:
Suspicious login pattern triggers Shield™, KAI correlates it with endpoint telemetry, and automatically isolates the device until resolved.
Backup & Recovery Coordination
Manages backups intelligently over constrained networks and ensures rapid recovery when needed.
Use Case Example:
Remote sites with unstable connections complete backups without manual intervention, while KAI predicts potential issues and alerts admins.
Multi-Cloud Governance
Unifies visibility and policy enforcement across multiple cloud providers with comprehensive drift detection.
Use Case Example:
Detect and remediate overly permissive IAM roles in AWS and Azure automatically before compliance violations occur.
DeviceScan™
Network discovery & inventory with automatic device detection via ARP, LLDP, SNMP-lite, and port sampling.
PilotView™
Guided workflows & automation for IT operations with step validation and KAI-suggested steps.
KAI™ Intelligence
Predictive analytics layer powering actionable recommendations across all platform modules.
KAI™ – Predictive Intelligence Layer
KAI™ powers predictive analytics and actionable recommendations across all modules, transforming how you manage IT operations.
Anomaly Detection
Across telemetry, security, backup, and cloud data with intelligent pattern recognition.
Root Cause Correlation
Connect incidents across modules to identify underlying issues and prevent recurrence.
Workflow Recommendations
Intelligent step suggestions in PilotView™ for optimized IT operations.
Predictive Alerts
Advanced warning systems in CommandView™, Pulse™, Vault™, and SkyEdge™.
Real-World Intelligence in Action
Issue Detection
KAI monitors backup success rates across remote sites
Pattern Correlation
Correlates backup failures with endpoint CPU spikes and tunnel instability
Predictive Alert
Generates alert 24-72 hours before potential service disruption
Automated Resolution
Suggests and can execute remediation steps via PilotView™
"KAI correlates backup failures, endpoint CPU spikes, and tunnel instability, alerting administrators before users experience downtime."
EdgeBox™ – Local Orchestration Device
A lightweight local appliance that ensures continuity in environments with poor connectivity, providing local caching of policies and telemetry buffering.
Offline-First Operation
Continue monitoring and automation during internet disruptions
Local Data Processing
Telemetry buffering and policy caching for offline resilience
Local KAI Inference
Optional local AI processing for predictive alerts without cloud dependency
Use Case Example:
An EdgeBox in a rural branch continues monitoring devices and queues events until network connectivity is restored, then syncs with the central management plane.

Transform Your IT Operations With Unified Intelligence
Join forward-thinking IT teams who are consolidating tools, reducing complexity, and achieving proactive operations with KonectIQ's unified platform
Why Organizations Choose KonectIQ
Consolidate Your Tool Sprawl
Replace multiple disconnected solutions with one unified platform that provides complete visibility and control.
Proactive Security Posture
Move from reactive security to predictive protection with AI-driven threat detection and automated remediation.
Built for Connectivity Challenges
Offline-first architecture ensures continuous operations even in areas with unreliable internet connectivity.
Data-Driven Decision Making
Transform raw telemetry into actionable insights with predictive analytics and intelligent recommendations.
Secure Your Early Access Position
Join the waitlist to receive priority access, special launch pricing, and the opportunity to shape our product roadmap with your feedback.
Designed for IT teams managing complex, distributed infrastructure